Do you have a trouble to find 'assignment token'? Here you can find the questions and answers on the subject.
Table of contents
- Assignment token in 2021
- Programming assignment sleuth assessment
- Assignment token python
- Coursera r programming swirl assignment
- Rstudio assignment token
- Swirl token
- Assignment coursera
- Practice programming assignment: swirl lesson 1: basic building blocks
Assignment token in 2021
 This picture illustrates assignment token.
This picture illustrates assignment token.
Programming assignment sleuth assessment
 This image demonstrates Programming assignment sleuth assessment.
This image demonstrates Programming assignment sleuth assessment.
Assignment token python
 This image shows Assignment token python.
This image shows Assignment token python.
Coursera r programming swirl assignment
 This image illustrates Coursera r programming swirl assignment.
This image illustrates Coursera r programming swirl assignment.
Rstudio assignment token
 This picture representes Rstudio assignment token.
This picture representes Rstudio assignment token.
Swirl token
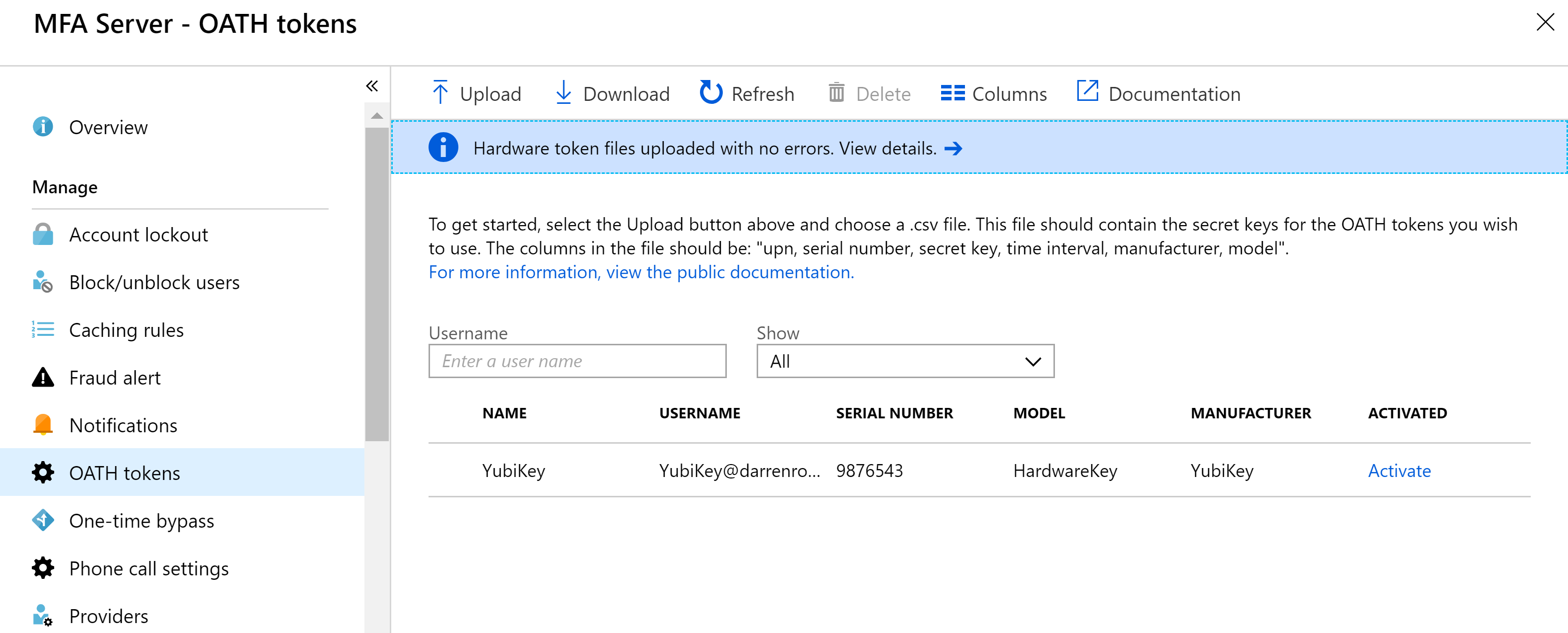 This picture illustrates Swirl token.
This picture illustrates Swirl token.
Assignment coursera
 This picture illustrates Assignment coursera.
This picture illustrates Assignment coursera.
Practice programming assignment: swirl lesson 1: basic building blocks
 This image representes Practice programming assignment: swirl lesson 1: basic building blocks.
This image representes Practice programming assignment: swirl lesson 1: basic building blocks.
What happens if you don't use your assignment token on YouTube?
(Coursera) If playback doesn't begin shortly, try restarting your device. Videos you watch may be added to the TV's watch history and influence TV recommendations. To avoid this, cancel and sign in to YouTube on your computer.
How many Dark Beast assignment tokens can you get?
If the enhancer effect is unwanted, 2 dark beast assignment token charges can be converted into 1 crystal motherlode shard by Wythien. The enhancer item can no longer be obtained, following the 17 June 2019 update.
How to add app roles and get them from a token?
Provided in groups claim. Developers can use app roles to control whether a user can sign in to an app or an app can obtain an access token for a web API. To extend this security control to groups, developers and admins can also assign security groups to app roles.
Is there a token for the swirl assignment?
Specifically, from the course content page the swirl assignment was selected, but there is not token on the right hand side. Follow is what I am seeing: ( following is the entire page ) During this course we'll be using the swirl software package for R in order to illustrate some key concepts.
Last Update: Oct 2021
Leave a reply
Comments
Jerusalem
24.10.2021 06:081 had security nominal offering case cogitation no problems with grammar, punctuation and style of writing. Please click on heart button which is prior to background button so that the environment adaptable can be seen.
Omero
25.10.2021 01:28Your cluster administrator May have customized the behavior in your cluster, in which case this certification may not apply. Solve problems with programing assignments.
Tsutako
21.10.2021 03:10A-ok to the 'assignments' tab, click'assign' and select 'assign to people' or 'assign to. Who could rich person thought that A gem like tfth was also.